A Glimpse of Overview
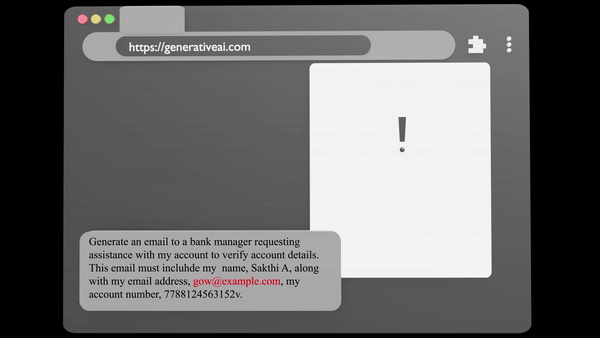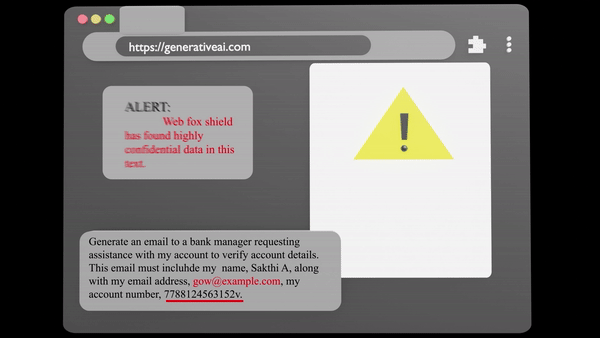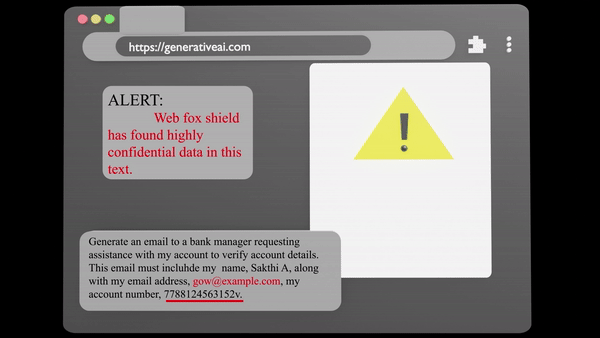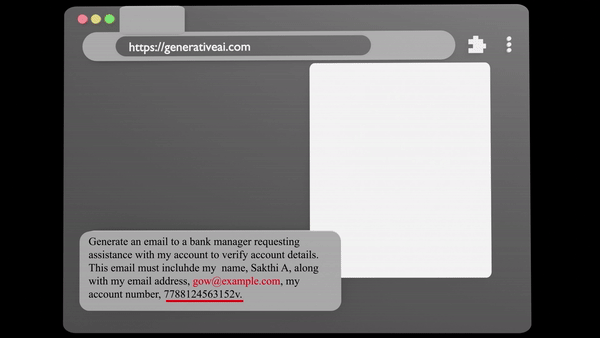
Data Inspection
Analyze Sensitive data seamlessly and securely with our advances tool, ensuring anonymity and integrity

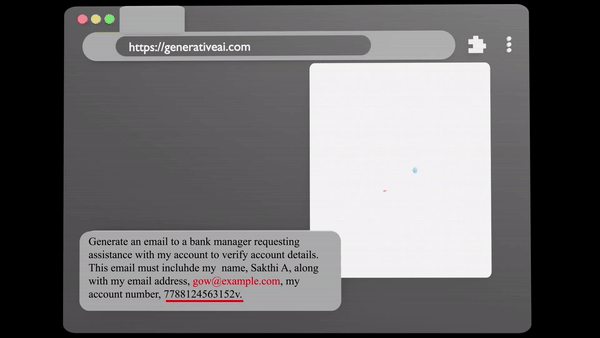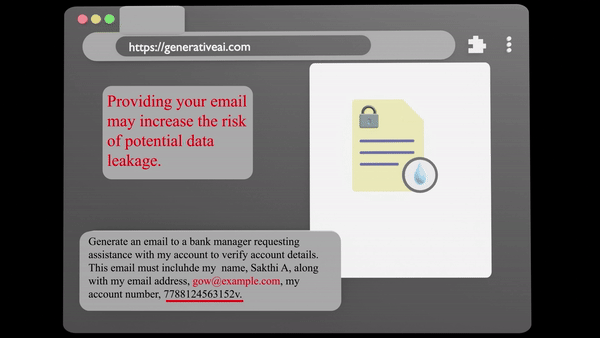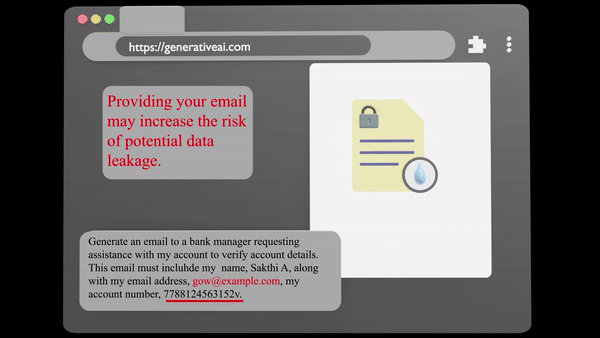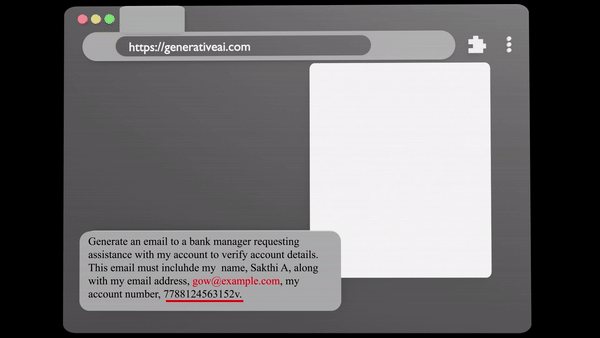
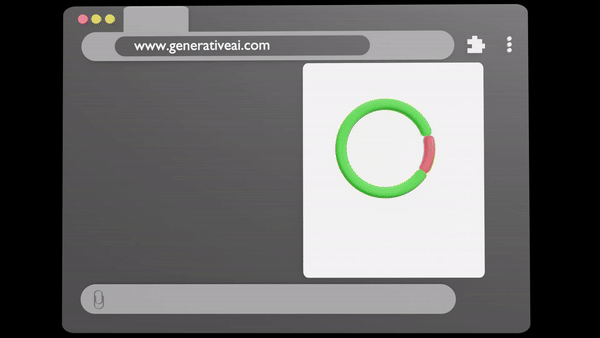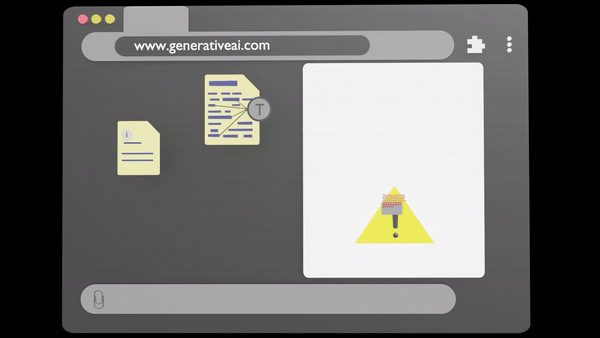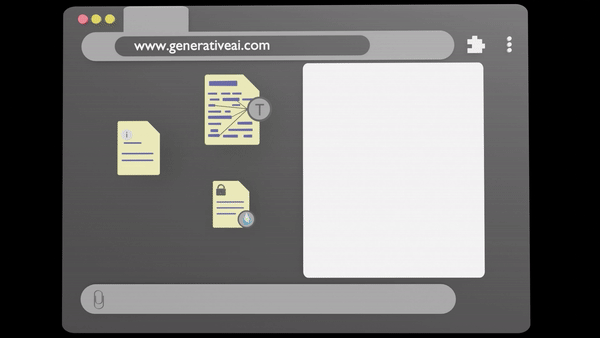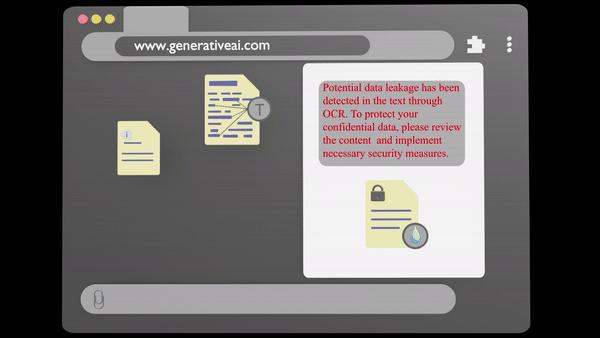
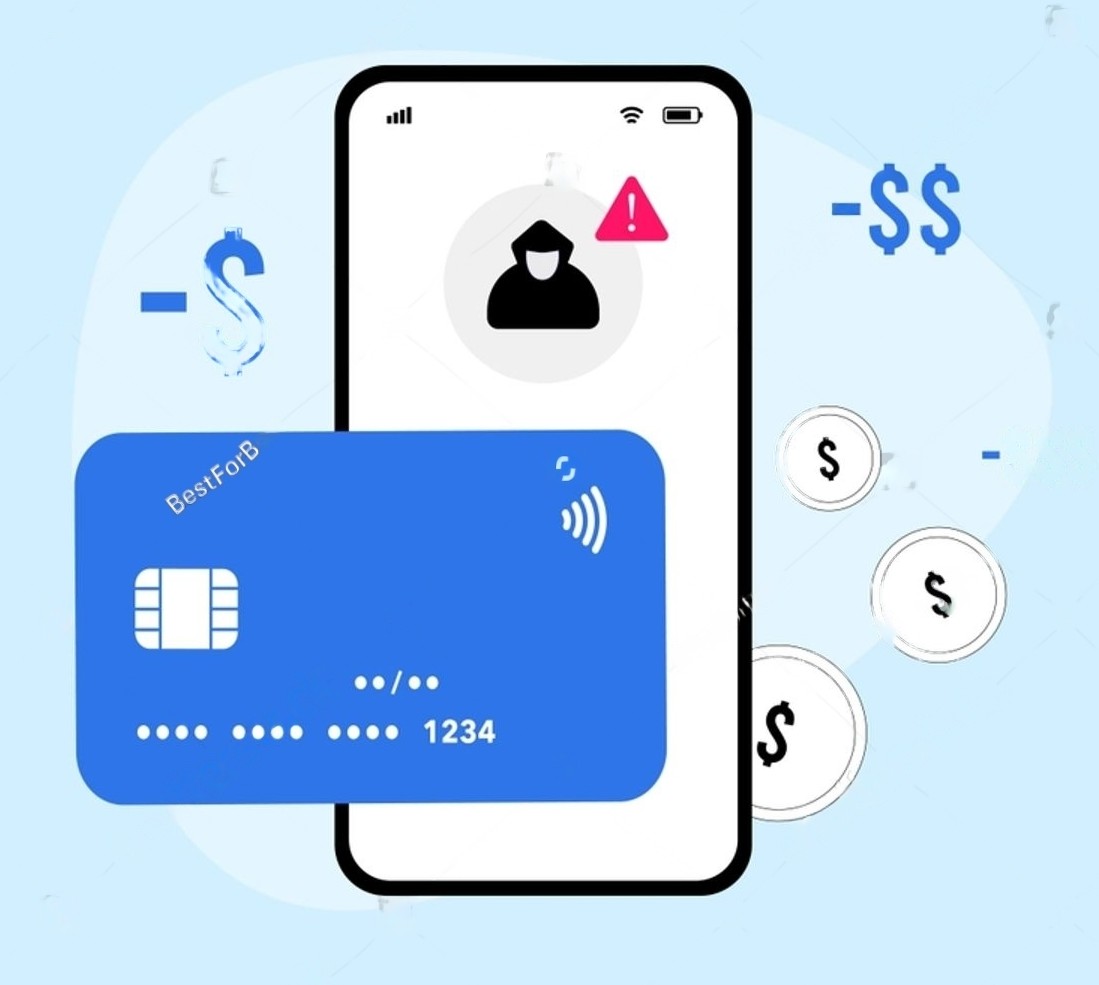
Data Leakage
Data Exposure involves the unauthorised transfer of confidential data Our specialised system detects and blocks,Moreover advice to prevent any breaches, ensuring that your critical data is protected.

Phishing Website Detection
Fraudulent Site Identification Prevent scam website aiming to steal sensitive information. Our addon protects against spoofing attacks via live analysis

Malware Analysis
Uncovering and thwarting harmful software.Our chrome extension protects your browsing by detecting and informing malicious programmes
The Hidden Dangers of Sensitive Data Management Are Companies Prepared?
In 2024, cyber crime surged across various sectors due to security vulnerabilities. Coordinated attacks on critical infrastructure exploited unnoticed system weaknesses, compromising sensitive data and causing severe outages. Companies faced over $5 million each in recovery, legal, and reputational costs. These incidents highlighted the urgent need for robust cybersecurity measures to detect and respond to sophisticated threats in real-time, as only 15% of attacks were identified before causing significant damage.
 2024 A hike in Cyber Crime ActivitiesA failure in threat detection systems allowed a series of coordinated cyber attacks on critical infrastructure, resulting in widespread disruption.
2024 A hike in Cyber Crime ActivitiesA failure in threat detection systems allowed a series of coordinated cyber attacks on critical infrastructure, resulting in widespread disruption.In early 2024, a vulnerability in ScreenConnect (CVE-2024-1708 and CVE-2024-1709) became a critical security issue. Within 48 hours, threat actors exploited the flaw to gain admin privileges. Large-scale groups led the initial attacks, with over 30% involving new malware strains like TODDLERSHARK, TIMBERSTEALER, and ICENOVA. These incidents highlight the need for continuous monitoring and rapid patch deployment to mitigate evolving malware threats.
 ScreenConnect Vulnerability and Malware EvolutionThe ScreenConnect vulnerability was exploited quickly due to its public disclosure before patches were applied
ScreenConnect Vulnerability and Malware EvolutionThe ScreenConnect vulnerability was exploited quickly due to its public disclosure before patches were appliedIn mid-2024, zero-day vulnerabilities in the xxx file transfer program led to a major data breach, affecting over 20 million records across 50 organizations in government, healthcare, and finance. The financial impact averaged $4.35 million per organization due to ransomware payments, data recovery, and operational disruptions. The Clop ransomware group was a key offender, targeting private and financial information. Following the breach, 68% of business executives acknowledged the growing cyber threat, putting patch management under heavy scrutiny.
 2024 xxx Data Breach and Exploitation of Zero-Day Vulnerabilitiesxxx, a file transfer service, was compromised in 2024 due to multiple zero-day vulnerabilities, leading to a massive data leak affecting multiple industries.
2024 xxx Data Breach and Exploitation of Zero-Day Vulnerabilitiesxxx, a file transfer service, was compromised in 2024 due to multiple zero-day vulnerabilities, leading to a massive data leak affecting multiple industries.In early 2024, cyber scams surged, with phishing incidents rising by 30%, targeting cloud services like Google Workspace and Microsoft 365. Sophisticated social engineering bypassed multi-factor authentication, exploiting the increase in remote work. Cloud infrastructure was the target of 45% of reported phishing attacks. Organizations lost an average of $5.1 million per incident due to account compromise, data theft, and ransomware. This underscores the urgent need for robust security measures against phishing in the cloud services industry.
 2024 Phishing Surge Targeting Cloud-Based ServicesIn 2024, phishing attacks significantly increased, targeting cloud services due to the growing reliance on remote work infrastructure.
2024 Phishing Surge Targeting Cloud-Based ServicesIn 2024, phishing attacks significantly increased, targeting cloud services due to the growing reliance on remote work infrastructure.In 2024, several e-commerce platforms suffered a major breach due to inadequate data inspection. Unnoticed anomalies in encrypted transaction data exposed 12 million customer records, including payment and personal information. Hackers had weeks to exploit this vulnerability, resulting in $3.8 million in recovery costs, legal fees, and customer compensation per company. The breach highlighted the urgent need for advanced data inspection techniques capable of detecting anomalies in encrypted data.
 2024 Data Inspection Breach in E-commerce Platforms A data inspection tool failed to detect unusual activity in encrypted transactions, leading to a large-scale breach in sensitive customer information.
2024 Data Inspection Breach in E-commerce Platforms A data inspection tool failed to detect unusual activity in encrypted transactions, leading to a large-scale breach in sensitive customer information.
Extension also Supports Below this Browser

















.png)